basic concept of router
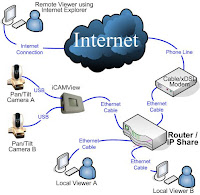
Lab Requirements: to be able to perform the tasks in this lab you need 2 Cisco routers connected to each other. In this TechLan we assumed two 2501 routers, but pretty much set of routers will do. This lab does not cover how to physically connect the routers and the hosts, but rather assumes you can tell by looking at the diagram. If you need information on how to setup your lab physically, please refer to our Setting up the Hardware TechLab.
This lab comes in three versions, the one you are looking at, a printer-friendly version with the commands, and a printer-friendly version without the commands that can be used as an assessment. The printer-friendly versions are for members only. Also note the the commands in this lab often include the router command prompt and never use the abbreviated form.
This first CCNA TechLab covers a couple of basic configuration tasks, such as setting passwords and enabling IP routing using RIP. You will need a lab setup similar to the network diagram below:
Before you start, make sure you clear both routers' configuration using the Router#erase startup-config command. First we will configure RouterA, after the router reboots, the following message will be displayed:
% Please answer 'yes' or 'no'.
Would you like to enter the initial configuration dialog? [yes/no]
Type no and press ENTER. Press ENTER again when the message Press RETURN to get started appears. Type enable at the Router> command prompt to enter Privileged Exec mode, notice the prompt chances to Router#.
CONFIGURING THE FIRST ROUTER
STEP 1. Change the router's host name to RouterA
Enter configuration mode using the following command:
Router#configure terminal
Change the host name of the router to RouterA using the following command :
Router(config)#hostname RouterA
RouterA(config)#
Notice how changing the hostname immediately affects the prompt. Remember that you are configuring the running configuration.
STEP 2. Disable domain lookups
To prevent the router from interpreting every incorrectly typed command as a host name and trying to resolve it to an IP address to setup a telnet connection with it, use the following command:
RouterA(config)#no ip domain-lookup
STEP 3. Configure passwords
First set the enable password to cisco123 using the following command:
RouterA(config)#enable secret cisco123
Next, set the password for telnet connections to cisco456 using the following commands:
RouterA(config)#line vty 0 4
RouterA(config-line)#password cisco456
RouterA(config-line)#login
Although the enable secret command is used to encrypt the enable password, other passwords stored in the router's configuration should be encrypted as well. To do this, use the following command:
RouterA(config)#service password-encryption
STEP 4. Configuring the Ethernet interface
Enter Interface configuration mode for the Ethernet interface, using the following command:
RouterA(config)#interface Ethernet 0
Give it the description "Connected to LAN" using the following command:
RouterA(config-if)#description Connected to LAN1
Configure the IP address (see diagram for correct address) for the interface using the following command:
RouterA(config-if)#ip address 192.168.11.1 255.255.255.0
Enable the interface using the following command:
RouterA(config-if)#no shutdown
STEP 5. Configure the serial WAN interface
Switch to Interface configuration mode for the first Serial interface, using the following command:
RouterA(config)#interface Serial 0
Give it the description "Direct connection to RouterB" using the following command:
RouterA(config-if)#description connected to RouterB
Configure the IP address (see diagram for correct address) for the interface using the following command:
RouterA(config-if)#ip address 192.168.22.5 255.255.255.0
Configure the interface to use PPP encapsulation using the following command:
RouterA(config-if)#encapsulation ppp
Enable the interface using the following command:
RouterA(config-if)#no shutdown
STEP 6. Configure RIP
Use the following command to enable RIP on RouterA:
RouterA(config)#router rip
Configure the router to receive and send only RIP Version 2 packets using the following command:
RouterA(config-router)#version 2
Use the following commands to specify the networks directly connected to the router:
RouterA(config-router)#network 192.168.11.0
RouterA(config-router)#network 192.168.22.0
STEP 7. Save configuration
To copy the currently running active configuration to NVRAM, so it will be used the next time you reload the router, use the following command:
RouterA#copy running-config startup-config
STEP 8. Configuration second router
To configure the other router, RouterB, repeat the steps above. Use the network diagram to determine the correct addressing and names. To enable the back-to-back serial connection between te routers, you need to configure one router as DCE using the following command in Interface configuration mode for the serial connection on RouterB:
RouterB(config-if)#clock rate 64000
STEP 9. Verify and test the configuration
Verify using the ping command Host A to Host B, make sure you configured both hosts to use the nearest router's interface as the default gateway in the TCP/IP settings.
On both routers, run the following command in Privileged Exec mode to determine which device is the DCE:
Router#show controllers s0
On one of the routers, run the following command in Privileged Exec mode to display the parameters and current state of the active routing protocol process, and examine the output:
Router#show ip protocols
Use the following command to verify routing table entries on both routers:
Router#show ip route
Use the following command to list a summary of the interface's IP information and status on both routers, and examine the output:
Router#show ip interface
Use the same command with the brief option, and the notice output:
Router#show ip interface brief
Tutorial Step By Step Seting MikroTik
* Firewall and NAT - stateful packet filtering; Peer-to-Peer protocol filtering; source and destination NAT; classification by source MAC, IP addresses (networks or a list of networks) and address types, port range, IP protocols, protocol options (ICMP type, TCP flags and MSS), interfaces, internal packet and connection marks, ToS (DSCP) byte, content, matching sequence/frequency, packet size, time and more…
* Routing - Static routing; Equal cost multi-path routing; Policy based routing (classification done in firewall); RIP v1 / v2, OSPF v2, BGP v4
* Data Rate Management - Hierarchical HTB QoS system with bursts; per IP / protocol / subnet / port / firewall mark; PCQ, RED, SFQ, FIFO queue; CIR, MIR, contention ratios, dynamic client rate equalizing (PCQ), bursts, Peer-to-Peer protocol limitation
* HotSpot - HotSpot Gateway with RADIUS authentication and accounting; true Plug-and-Play access for network users; data rate limitation; differentiated firewall; traffic quota; real-time status information; walled-garden; customized HTML login pages; iPass support; SSL secure authentication; advertisement support
* Point-to-Point tunneling protocols - PPTP, PPPoE and L2TP Access Concentrators and clients; PAP, CHAP, MSCHAPv1 and MSCHAPv2 authentication protocols; RADIUS authentication and accounting; MPPE encryption; compression for PPPoE; data rate limitation; differentiated firewall; PPPoE dial on demand
* Simple tunnels - IPIP tunnels, EoIP (Ethernet over IP)
* IPsec - IP security AH and ESP protocols; MODP Diffie-Hellman groups 1,2,5; MD5 and SHA1 hashing algorithms; DES, 3DES, AES-128, AES-192, AES-256 encryption algorithms; Perfect Forwarding Secrecy (PFS) MODP groups 1,2,5
* Proxy - FTP and HTTP caching proxy server; HTTPS proxy; transparent DNS and HTTP proxying; SOCKS protocol support; DNS static entries; support for caching on a separate drive; access control lists; caching lists; parent proxy support
* DHCP - DHCP server per interface; DHCP relay; DHCP client; multiple DHCP networks; static and dynamic DHCP leases; RADIUS support
* VRRP - VRRP protocol for high availability
* UPnP - Universal Plug-and-Play support
* NTP - Network Time Protocol server and client; synchronization with
GPS system
* Monitoring/Accounting - IP traffic accounting, firewall actions logging, statistics graphs accessible via HTTP
* SNMP - read-only access
* M3P - MikroTik Packet Packer Protocol for Wireless links and Ethernet
* MNDP - MikroTik Neighbor Discovery Protocol; also supports Cisco Discovery Protocol (CDP)
* Tools - ping; traceroute; bandwidth test; ping flood; telnet; SSH; packet sniffer; Dynamic DNS update tool
Layer 2 connectivity:
* Wireless - IEEE802.11a/b/g wireless client and access point (AP) modes; Nstreme and Nstreme2 proprietary protocols; Wireless Distribution System (WDS) support; virtual AP; 40 and 104 bit WEP; WPA pre-shared key authentication; access control list; authentication with RADIUS server; roaming (for wireless client); AP bridging
* Bridge - spanning tree protocol; multiple bridge interfaces; bridge firewalling, MAC
* VLAN - IEEE802.1q Virtual LAN support on Ethernet and wireless links; multiple VLANs; VLAN bridging
* Synchronous - V.35, V.24, E1/T1, X.21, DS3 (T3) media types; sync-PPP, Cisco HDLC, Frame Relay line protocols; ANSI-617d (ANDI or annex D) and Q933a (CCITT or annex A) Frame Relay LMI types
* Asynchronous - s*r*al PPP dial-in / dial-out; PAP, CHAP, MSCHAPv1 and MSCHAPv2 authentication protocols; RADIUS authentication and accounting; onboard s*r*al ports; modem pool with up to 128 ports; dial on demand
* ISDN - ISDN dial-in / dial-out; PAP, CHAP, MSCHAPv1 and MSCHAPv2 authentication protocols; RADIUS authentication and accounting; 128K bundle support; Cisco HDLC, x75i, x75ui, x75bui line protocols; dial on demand
* SDSL - Single-line DSL support; line termination and network termination modes
Instalasi dapat dilakukan pada Standard computer PC yang akan dijadikan router dan tidak memerlukan resource yang cukup besar untuk penggunaan standard, misalnya hanya sebagai gateway.
Berikut spec_minimal nya :
* CPU dan motherboard - bisa dgn P1 ~ P4, AMD, cyrix asal yang bukan multi-prosesor
* RAM - minimum 32 MiB, maximum 1 GiB; 64 MiB atau lebih sangat dianjurkan, kalau mau sekalian dibuat proxy , dianjurkan 1GB… perbandingannya, 15MB di memori ada 1GB di proxy..
* HDD minimal 128MB parallel ATA atau Compact Flash, tidak dianjurkan menggunakan UFD, SCSI, apa lagi S-ATA (mungkin nanti Ver. 3.0)
* NIC 10/100 atau 100/1000
Untuk keperluan beban yang besar ( network yang kompleks, routing yang rumit dll) disarankan untuk mempertimbangkan pemilihan resource PC yang memadai.
Lebih lengkap bisa dilihat di www.mikrotik.com. Meskipun demikian Mikrotik bukanlah free software, artinya kita harus membeli licensi terhadap segala fasiltas yang disediakan. Free trial hanya untuk 24 jam saja.
Kita bisa membeli software MikroTik dalam bentuk “licence” di CITRAWEB, UFOAKSES, PC24 (atau download cracknya, he he he …) yang diinstall pada HardDisk yang sebelumnya download/dibuat MikroTik RouterOS ISO kekeping CD atau disk on module (DOM). Jika kita membeli DOM tidak perlu install tetapi tinggal pasang DOM pada slot IDE PC kita.
Langkah-langkah berikut adalah dasar-dasar setup mikrotik yang dikonfigurasikan untuk jaringan
sederhana sebagai gateway server.
1. Langkah pertama adalah install Mikrotik RouterOS pada PC atau pasang DOM.
2. Login Pada Mikrotik Routers melalui console :
MikroTik v2.9.39
Login: admin
Password: (kosongkan)
Sampai langkah ini kita sudah bisa masuk pada mesin Mikrotik. User default adalah admin dan tanpa password, tinggal ketik admin kemudian tekan tombol enter.
3. Untuk keamanan ganti password default
[admin@Mikrotik] > password
old password: *****
new password: *****
retype new password: *****
[admin@ Mikrotik] >
4. Mengganti nama Mikrotik Router, pada langkah ini nama server akan kita ganti menjadi
“r-WLI” (bebas, disesuaikan dengan nama jaringan kita…)
[admin@Mikrotik] > system identity set name=r-WLI
[admin@r-WLI] >
5. Melihat interface pada Mikrotik Router
[admin@r-WLI] > interface print
Flags: X - disabled, D - dynamic, R - running
# NAME TYPE RX-RATE TX-RATE MTU
0 R ether1 ether 0 0 1500
1 R ether2 ether 0 0 1500
[admin@r-WLI] >
6. Memberikan IP address pada interface Mikrotik. Misalkan ether1 akan kita gunakan untuk koneksi ke Internet dengan IP 192.168.0.1 dan ether2 akan kita gunakan untuk network local kita dengan IP 172.16.0.1
[admin@r-WLI] > ip address add address=192.168.0.1 /
netmask=255.255.255.0 interface=ether1
[admin@r-WLI] > ip address add address=172.16.0.1 /
netmask=255.255.255.0 interface=ether2
7. Melihat konfigurasi IP address yang sudah kita berikan
[admin@r-WLI] >ip address print
Flags: X - disabled, I - invalid, D - dynamic
# ADDRESS NETWORK BROADCAST INTERFACE
0 192.168.0.1/24 192.168.0.0 192.168.0.63 ether1
1 172.16.0.1/24 172.16.0.0 172.16.0.255 ether2
[admin@r-WLI] >
8. Memberikan default Gateway, diasumsikan gateway untuk koneksi internet adalah 192.168.0.254
[admin@r-WLI] > /ip route add gateway=192.168.0.254
9. Melihat Tabel routing pada Mikrotik Routers
[admin@r-WLI] > ip route print
Flags: X - disabled, A - active, D - dynamic,
C - connect, S - static, r - rip, b - bgp, o - ospf
# DST-ADDRESS PREF-SRC G GATEWAY DISTANCE INTERFACE
0 ADC 172.16.0.0/24 172.16.0.1 ether2
1 ADC 192.168.0.0/26 192.168.0.1 ether1
2 A S 0.0.0.0/0 r 192.168.0.254 ether1
[admin@r-WLI] >
10. Tes Ping ke Gateway untuk memastikan konfigurasi sudah benar
[admin@r-WLI] > ping 192.168.0.254
192.168.0.254 64 byte ping: ttl=64 time
11. Setup DNS pada Mikrotik Routers
[admin@r-WLI] > ip dns set primary-dns=192.168.0.10 /
allow-remoterequests=no
[admin@r-WLI] > ip dns set secondary-dns=192.168.0.11 /
allow-remoterequests=no
12. Melihat konfigurasi DNS
[admin@r-WLI] ip dns> pr
primary-dns: 192.168.0.10
secondary-dns: 192.168.0.11
allow-remote-requests: no
cache-size: 2048KiB
cache-max-ttl: 1w
cache-used: 21KiB
[admin@r-WLI] ip dns>
13. Tes untuk akses domain, misalnya dengan ping nama domain
[admin@r-WLI] > ping yahoo.com
216.109.112.135 64 byte ping: ttl=48 time=250 ms
10 packets transmitted, 10 packets received, 0% packet loss
round-trip min/avg/max = 571/571.0/571 ms
[admin@r-WLI] >
Jika sudah berhasil reply berarti seting DNS sudah benar.
14. Setup Masquerading, Jika Mikrotik akan kita pergunakan sebagai gateway server maka agar client computer pada network dapat terkoneksi ke internet perlu kita masquerading.
[admin@r-WLI]> ip firewall nat add action=masquerade /
outinterface=ether1 chain:srcnat
[admin@r-WLI] >
15. Melihat konfigurasi Masquerading
[admin@r-WLI]ip firewall nat print
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat out-interface=ether1 action=masquerade
[admin@r-WLI] >
Setelah langkah ini bisa dilakukan pemeriksaan untuk koneksi dari jaringan local. Dan jika berhasil berarti kita sudah berhasil melakukan instalasi MikroTik Router sebagai Gateway server. Setelah terkoneksi dengan jaringan Mikrotik dapat dimanage menggunakan WinBox yang bisa didownload dari MikroTik.com atau dari server mikrotik kita.
Misal Ip address server mikrotik kita 192.168.0.1, via browser buka http://192.168.0.1 dan download WinBox dari situ.
Jika kita menginginkan client mendapatkan IP address secara otomatis maka perlu kita setup dhcp server pada Mikrotik. Berikut langkah-langkahnya :
1. Buat IP address pool
/ip pool add name=dhcp-pool ranges=172.16.0.10-172.16.0.20
2. Tambahkan DHCP Network dan gatewaynya yang akan didistribusikan ke client Pada contoh ini networknya adalah 172.16.0.0/24 dan gatewaynya 172.16.0.1
/ip dhcp-server network add address=172.16.0.0/24 gateway=172.16.0.1
3. Tambahkan DHCP Server ( pada contoh ini dhcp diterapkan pada interface ether2 )
/ip dhcp-server add interface=ether2 address-pool=dhcp-pool
4. Lihat status DHCP server
[admin@r-WLI] > ip dhcp-server pr
Flags: X - disabled, I - invalid
# NAME INTERFACE RELAY ADDRESS-POOL LEASE-TIME ADD-ARP
x dhcp1 ether2 dhcp_pool1 4w2d yes
[admin@r-WLI] >
Tanda X menyatakan bahwa DHCP server belum enable maka perlu dienablekan terlebih dahulu pada langkah 5.
5. Jangan Lupa dibuat enable dulu dhcp servernya
/ip dhcp-server enable 0
Kemudian cek kembali dhcp-server seperti langkah 4, jika tanda X sudah tidak ada berarti sudah aktif.
6. Tes Dari client
Run dari Comman Prompt
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\Documents and Settings\EsDat>ping www.yahoo.com
Pinging www.yahoo-ht3.akadns.net [69.147.114.210] with 32 bytes of data:
Reply from 124.158.129.5: bytes=32 time=34ms TTL=59
Reply from 124.158.129.5: bytes=32 time=24ms TTL=59
Reply from 124.158.129.5: bytes=32 time=41ms TTL=59
Reply from 124.158.129.5: bytes=32 time=29ms TTL=59
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 24ms, Maximum = 41ms, Average = 32ms
7. Untuk bandwith controller, bisa dengan sistem simple queue ataupun bisa dengan mangle
[admin@r-WLI] queue simple> add name=Komputer01 /
interface=ether2 target-address=172.16.0.1/24 max-limit=65536/131072
[admin@r-WLI] queue simple> add name=Komputer02 /
interface=ether2 target-address=172.16.0.2/24 max-limit=65536/131072
dan seterusnya…
lengkap nya ada disini
www.mikrotik.com/docs/ros/2.9/root/queue
linux-ip.net/articles/Traffic…/overview.html
luxik.cdi.cz/~devik/qos/htb
www.docum.org/docum.org/docs
PC based Robotic

White Box Robotics was founded in 2000 to give the mobile robotics industry a hard shove forward. We want to give enthusiasts a radical tool that breaks down walls and allows people to build advanced mobile robots. Our mission is to develop mobile robotic platforms that empower people by eliminating the difficult learning curve associated with building these machines. Our focus is to create and develop PC-BOTs- plug-and-play robots created almost entirely from off-the-shelf computer parts. This technology allows anyone with a rudimentary understanding of assembling or upgrading PCs to build this new species of robot. The 9-series PC-BOT is a standard for the world which allows us to focus our energies on a common platform.
We are all pioneers, daredevils, and evangelists for this movement. As a community we have the privilege of changing the very fabric of society…just like the early PC enthusiasts did in the 1970s. We have the opportunity to improve the quality of people’s lives through robotics. We will actively contribute to this amazing future where robots will be a part of our everyday existence…assisting the elderly, providing companionship, and protecting the innocent.
If you are reading this, chances are you understand that White Box Robotics is about sharing a common passion for these wonderful machines. The 9-series isn’t merely a cold conglomeration of sheet metal and electronics. It’s a companion we’ve longed to know all our lives. It’s a living thing…the fruit of a labor of love.
It’s about the turn of the wrench, the feel of the screwdriver in your hand…working with earthly elements- copper, steel, silver, lead, and oil that is this spectacular machine. It’s about manipulating these materials in such a way to create life. You lovingly build this modern machine and watch it live, move, interact with the world. For just an intoxicating second it takes you somewhere else. You feel shifted…suspended, briefly glancing twenty-five years into the future. Somehow you’ve had the privilege to build a machine that feels so miracously alive! This is the empowering gift we wish to give. This is what we mean when we invite you to Dream in White.
We will always make sure that White Box Robotics does its part by consistently developing world-class platforms and accessories. This platform…this robot is not the end of five years of passionate development- it is merely the beginning. One robot in a series of many…ever evolving…the product of the dreams of the many.
Our hope is to fuse the talents of two mighty communities- PC enthusiasts and robotics enthusiasts- into one empowered driving force. This community is comprised of talent diverse as the technology itself- mechanical engineers, scientists, researchers, hackers, modders, electrical engineers, software engineers, and enthusiasts the world over. By joining forces we have the opportunity to birth an industry. We will all work together and mountains will move.
Challenge yourself in more rewarding directions and BE the change you want to see. I believe we can change the world one robot at a time.
What is a COMPUTER VIRUS?

A computer virus is a computer program that can copy itself and infect a computer without permission or knowledge of the user. However, the term "virus" is commonly used, albeit erroneously, to refer to many different types of malware programs. The original virus may modify the copies, or the copies may modify themselves, as occurs in a metamorphic virus.
A virus can only spread from one computer to another when its host is taken to the uninfected computer, for instance by a user sending it over a network or the Internet, or by carrying it on a removable medium such as a floppy disk, CD, or USB drive. Meanwhile viruses can spread to other computers by infecting files on a network file system or a file system that is accessed by another computer. Viruses are sometimes confused with computer worms and Trojan horses. A worm can spread itself to other computers without needing to be transferred as part of a host, and a Trojan horse is a file that appears harmless. Both worms and Trojans will cause harm to computers when executed.
Most personal computers are now connected to the Internet and to local area networks, facilitating the spread of malicious code. Today's viruses may also take advantage of network services such as the World Wide Web, e-mail, Instant Messaging and file sharing systems to spread, blurring the line between viruses and worms. Furthermore, some sources use an alternative terminology in which a virus is any form of self-replicating malware.
Some viruses are programmed to damage the computer by damaging programs, deleting files, or reformatting the hard disk. Others are not designed to do any damage, but simply replicate themselves and perhaps make their presence known by presenting text, video, or audio messages. Even these benign viruses can create problems for the computer user. They typically take up computer memory used by legitimate programs. As a result, they often cause erratic behavior and can result in system crashes. In addition, many viruses are bug-ridden, and these bugs may lead to system crashes and data loss.
Strategy of viruses
Stealth
Some viruses try to trick anti-virus software by intercepting its requests to the operating system. A virus can hide itself by intercepting the anti-virus software’s request to read the file and passing the request to the virus, instead of the OS. The virus can then return an uninfected version of the file to the anti-virus software, so that it seems that the file is "clean". Modern anti-virus software employs various techniques to counter stealth mechanisms of viruses. The only completely reliable method to avoid stealth is to boot from a medium that is known to be clean.
Self-modification
Most modern antivirus programs try to find virus-patterns inside ordinary programs by scanning them for so-called virus signatures. A signature is a characteristic byte-pattern that is part of a certain virus or family of viruses. If a virus scanner finds such a pattern in a file, it notifies the user that the file is infected. The user can then delete, or (in some cases) "clean" or "heal" the infected file. Some viruses employ techniques that make detection by means of signatures difficult but probably not impossible. These viruses modify their code on each infection. That is, each infected file contains a different variant of the virus.
Encryption with a variable key
A more advanced method is the use of simple encryption to encipher the virus. In this case, the virus consists of a small decrypting module and an encrypted copy of the virus code. If the virus is encrypted with a different key for each infected file, the only part of the virus that remains constant is the decrypting module, which would (for example) be appended to the end. In this case, a virus scanner cannot directly detect the virus using signatures, but it can still detect the decrypting module, which still makes indirect detection of the virus possible. Since these would be symmetric keys, stored on the infected host, it is in fact entirely possible to decrypt the final virus, but that probably isn't required, since self-modifying code is such a rarity that it may be reason for virus scanners to at least flag the file as suspicious.
An old, but compact, encryption involves XORing each byte in a virus with a constant, so that the exclusive-or operation had only to be repeated for decryption. It is suspicious code that modifies itself, so the code to do the encryption/decryption may be part of the signature in many virus definitions.
Polymorphic code
Polymorphic code was the first technique that posed a serious threat to virus scanners. Just like regular encrypted viruses, a polymorphic virus infects files with an encrypted copy of itself, which is decoded by a decryption module. In the case of polymorphic viruses however, this decryption module is also modified on each infection. A well-written polymorphic virus therefore has no parts which remain identical between infections, making it very difficult to detect directly using signatures. Anti-virus software can detect it by decrypting the viruses using an emulator, or by statistical pattern analysis of the encrypted virus body. To enable polymorphic code, the virus has to have a polymorphic engine (also called mutating engine or mutation engine) somewhere in its encrypted body. See Polymorphic code for technical detail on how such engines operate.
Some viruses employ polymorphic code in a way that constrains the mutation rate of the virus significantly. For example, a virus can be programmed to mutate only slightly over time, or it can be programmed to refrain from mutating when it infects a file on a computer that already contains copies of the virus. The advantage of using such slow polymorphic code is that it makes it more difficult for anti-virus professionals to obtain representative samples of the virus, because bait files that are infected in one run will typically contain identical or similar samples of the virus. This will make it more likely that the detection by the virus scanner will be unreliable, and that some instances of the virus may be able to avoid detection.
Metamorphic code
To avoid being detected by emulation, some viruses rewrite themselves completely each time they are to infect new executables. Viruses that use this technique are said to be metamorphic. To enable metamorphism, a metamorphic engine is needed. A metamorphic virus is usually very large and complex. For example, W32/Simile consisted of over 14000 lines of Assembly language code, 90% of which is part of the metamorphic engine.
Uploaded by TheEye23
COMPUTER HARDWARE
1. The government has taken aggressive steps in providing quality infrastructure with “Hardware Parks” flexible labor policies, availability of skilled workers, congenial business environment, level playing field, right policies and incentives, concessional import duty, reduction in excise duty, customs, SAD, CVD and sales tax. All these factors will make the market respond positively, economics of scale will come into play and big hardware companies will be attracted to set up local manufacturing units. That would result in high demand of computer hardware and subsequently prices would come down and make it affordable for a general customer.
2. Another major segment is “SCHOOLS & COLLEGES”. According to cll, if 20 PCs are installed in each of the country’s 9, 00,000 schools, the immediate demand would be 18 million, 10 times the current market figure.
3. Increase in the use of IT technologies in the government’s interface with the public has also stimulated the demand for computer hardware.
Migration from the old manual system to computing is taking place in large portion of government –public interaction, especially in providing statutory services such as land records, property transactions, authentication services, dealings of publicly owned utilities, collections of variety of taxes and transportation (Railways, Roadways and Airways etc). it will lead to a phenomenal demand for increase in hardware and would provide a big boost to the sagging national economy.
Central processing unit
There are many vendor of the cpu in the market same of them are
Intel, AMD, VIA/CYRIX, Transumeta / Motorola but the most popular are Intel and AMD Athelon. The X86 CPU architecture invented by Intel is the most popular for desktop computers today all the computers run the windows_9X operating system use X86 CPU
Intel corporation manufactured various kind of CPU’s but in market the most selling CPU we are concerning. P-3 , Celeron and P-4
Celeron processor is a substitution of P-3 having same performance so Celeron is taking place of P-3.
When P-4 came the total architecture is different from P-3.
P-3 has 0.18 micron technology and the P-4 has 0.13 micron technology.
P-4 if focused on multimedia, multitasking, multithreading. This gives batter performance in gaming, internet computing speed.
SYNTAX FOR CPU RECOGNITION
Name – speed in MHz/cache (KB)/FSB
e.g. --- Intel Pentium 3 –1133/256/100
CACHE MEMORY OF CPU
This is a memory associated with CPU, and often the motherboard. This is a type of memory that’s used to hold a duplicate of a larger store. This is faster than the main memory .By placing the most often accessed data in the cache memory, overall system speed increases.
Type of cache memory.
(1) L1 cache
(2) L2 cache
L1 CACHE MEMORY (LEVEL 1 CACHE)
This is closet to the CPU is the level 1 or L1 since 80486 an L1 cache has been built in to the CPU itself. This cache run at the CPU’s internal speed and so is very fast.
Celeron ---------- L1 cache is 16KB+16KB
Pentium 3 ------- L1 cache is 16KB+16KB
AMD athlon----- L1 cache is 128KB
Since L1 cache is part of the CPU it can’t be expanded or replaced.
L2 CACHE MEMORY (LEVEL 2 CACHES)
A L2 cache is more copious than an L1 cache, but it’s also slower. For CPU after Pentium Processor this is coated on the CPU package.
CPU L2 CACHE SIZE
PENTIUM-3 256-512KB
CELERON 0-128KB
AMD ATHLON 512KB
Placing the L2 cache on the CPU module improves performance relative to putting it on the motherboard largely because the cache can operate at a faster speed.
FSB (FRONT SIDE BUS)/ CPU BUS
Modern CPU’S run at two separate speeds: the core speed and the bus speed. The core speed is the no. associate most strongly with the CPU and is the speed at which most of CPU circuitry runs. The bus speed is the speed of interface between CPU and the motherboard. Now a days bus speed range from 66 MHz
To theoretical maximum of 400 MHz for slot A.(Main socket).
In order to set the CPU core speed motherboard includes jumpers or BIOS settings to specify a clock multiplier. The CPU runs its core at the bus speed multiplied by the clock multiplier.
E.g. 113.3MHz bus speed with a 10X clock gives CPU speed 1133 MHz(core speed).
CPU VOLTAGE
+Vcc supply to CPU is +5v and V core = 1.7 v.
As the CPU speed increases it becomes desirable to reduce the CPU voltage. In order to reduce the heat buildup inside the chips. For cooling a heat sink fan is mounted on the CPU.
MEMORY.
IDEA BEHIND BIOS
ROM-BIOS It is short form for read only memory -basic input output system. The ROM-BIOS is a set of Program built into the computer ROM memory that Provides the most basic, low level and intimate control And supervision operation for the computer.
=>The task of the bios is to take care of the immediate needs of the hardware and to isolate all other programs from the details of how the hardware works.
=>fundamentally the bios is an interface a connection and a Translator between the computer hardware and the software Programs.
PARTS OF BIOS
There are three main part of the ROM-bios program.
First part:
# This part is used only when the computer is first turned ON; these are Test and Initialization program that check to see that the computer is working. The delay between powering on the computer and The moment when it start working for you is due to running of these test and initialization program which sometimes are Called the POWER ON SELF TEST (POST).
Second part:-
# Important parts of the bios are its routimes.These programs provides the detailed and intimate control of The various part of the computer, particularly for the input/output Peripherals, such as the disk drives.
Third part:
# Rom-bios are the boot strap loader program.
Basic content of bios:
Standard CMOS feature.
Advanced bios feature.
Advanced chipset feature.
Integrated peripherals.
Power management setup.
PnP /PCI configuration.
Pc health status.
Frequency/voltage control.
Load optimized default.
Set supervisor password.
Set user password.
Save & exit setup.
Exit without saving.
Booting:
# The time duration between the appearance of the dos prompt or any window and the switch on the power supply the whole process is known as the booting process.
TYPE OF BOOTING
A) COLD BOOTING
B) WARM BOOTING
COLD BOOTING:
# When we switch off the computer completely and properly after some time we start Computer again is known as the cold booting.
WARM BOOTING:
# When we restart the computer from the restart button or using the key by simply pressing them i.e. ctrl+alt+del key is known as warm Booting.
MINIMUM REQUIREMENT FOR BOOTING:
For booting we required minimum three files-
1) ms_dos.sys
2) io.sys
3) Command.com
In these files first two files are hidden files and the third one is normal file.
MOTHERBOARD
If the CPU is the heart of the system the motherboard is its circulatory system. The CPU has to be fitted on the socket on the Board. The board has input output ports, ram, PCI slots, IDE port, chipset, Power connector, AGP slot, other expansion slots, floppy port.
The key features of the motherboard.
1. Socket
2. memory support
3. expansion slots
4. onboard IDE channels
5. Power supply and Power management
6. chipset
7. BIOS
8. Battery
9. Input/output ports.
SECONDARY STORAGE DEVICE
HARD DISK DRIVE
Hard disk are thin but rigid metal platters covered with a substances
That allows data to be held in the form of magnetized spots. Hard disk are
Tightly sealed within an enclosed hard disk drive unit to prevent any foreign
Matter from getting inside Data may be recorded on both sides of the disk
Platters. These platters are made of either using glass or aluminum.
A head crash happens when the surface of the read write head or particles on its surface come into contact within the surface of the hard disk platter, causing the loss of some or all of the data on the disk.
Both EIDE(enhanced integrated device electronics) and SCSI(small computer System interface) disks suffer from the limit of 1024 cylinder. The difficulty is that the old CHS (cylinder/head/sector) addressing mode uses a 10 bit number can hold a value of between 0 and 1023 , So the number of cylinders accessible by the BIOS is limited to 1024 hard disk performance measurements are-
(1) disk head seek time
(2) data transfer rate
(3) disk’s cache size.
Disk head seek time
Time taken to seek the data by move the head is referred as the seek time. The seek Time measurement that’s most often used is the average seek time, which is
Warnet bisnis mudah

Warnet adalah singkatan dari warung internet. Tempat dimana kita dapat mengkases internet dengan membayar sewa peralatan untuk mengaksesnya. Peralatan WARNET untuk mengakses internet adalah computer. Komputer warnet digunakan sebagai gerbang untuk mengakses informasi ke dunia internet. Jadi, dengan membayar sewa computer kita dapat mengakses internet melalui computer yang telah disediakan untuk mendapatkan informasi dari seluruh dunia.
Perkembangan warnet semakin meroket tajam. Mulai banyak orang yang mengetahui betapa menggiurkannya bisnis warnet ini, seiring dengan bertambahnya pemanfaatan internet. Bayangkan saja, target pasarnya luas. Dari para mahasiswa yang mencari bahan untuk tugas kuliahnya, remaja yang saling berkomunikasi lewat chating, hingga anak-anak yang bermain game online dengan teman-temannya dari seluruh penjuru tanah air bahkan dunia. Di era globalisasi ini internet tidak lagi sebagai kebutuhan pelengkap, namun mutlak menjadi kebutuhan pokok untuk mencapai kemjuan informasi.
Teknologi yang diperlukan untuk mendirikan WARNET tergolong cukup mudah dipelajari dan alat-alatnya pun sudah banyak dijual bebas. Intinya ada dua hal pokok agar warnet bias beroperasi, yaitu computer dan Koneksi internet. Untuk teknologi computer, sudah banyak didirikan kursus-kursus untuk mempelajarinya. Seperti, bagaimana men-setup jaringan, menginstal software computer, hingga menghilangkan virus. Sedangkan untuk memperoleh aliran bandwidth, juga sudah banyak perusahaan yang menyediakan. Tinggal telpon saja, dalam beberapa hari koneksi internet sudah mengalir ke tempat anda, dan warnet siap dijalankan.
Mudah bukan?. Bagi temen-temen yang ingin mendirikan bisnis warnet dan masih banyak waktu untuk belajar, silahkan pelajari teknologinya. Namun bagi yang tidak ada waktu dan ingin focus di bisnisnya, bisa memakai jasa setup warnet. Tinggal Pilih !!!
Keamanan Komputer
Apa itu keamanan computer!!
Keamanan computer adalah tindakan pencegahan dari ancaman yang dapat merusak bahkan menghapus file – file yang ada pada computer.
Sudah amankah Computer anda!!!
Pertanyaan itu mungkin dengan sangat mudah kita jawab “Ya” tanpa meninjau kembali tingkat keamanan computer kita dari berbagai ancaman. Ada beberapa ancaman yang dapat mengganggu keamanan Computer, yaitu sebagai berikut :
1. Ancaman dari gangguan alam ( Natural Disaster Threat )
- Terjadinya banjir
- Gempa Bumi
2. Ancaman Manusia ( Human Threat )
- Human Error, kesilapan
- Pemakaian computer oleh teman yang belum begitu mengerti computer
3. Virus Computer
Untuk menghindari dari beberapa ancaman diatas kita dapat melakukan langkah – langkah berikut ini:
1. Back up data anda kedalam media penyimpanan yang lain
- seperti : cd, dvd, hardisk external, atau flaskdisk
2. Selalu Update Antivirus yang anda gunakan
3. Gunakan Password untuk melakukan Login Computer Anda
- bila perlu tambah user untuk mengakses computer anda ( 1 login user & 1 lagi login
administrator yang diberi password )
4. Protect / kunci folder yang dianggap rahasia
5. Posisi / letak Computer
Cukup sampai disini Tips dari saya, lain kali akan disambung lagi.
Maintenance tasks that improve performance
If your computer seems slower than it used to be, it probably is. Over time, computers get slower because files become disorganized and resources are consumed by unnecessary software. Fortunately,Microsoft Windows XP includes tools to clean up your computer and restore its performance. The five steps in this article will walk you through the use of these tools to tune up your computer.
Before you do anything, back up your computer. Some of the steps in this article can cause pre-existing but hidden problems to surface, which may keep your computer from starting. A backup allows you to restore your important files in the unlikely event that something does go wrong.
1. Remove unused programs
First, remove programs you don't use anymore. Programs take up space on your computer, and some run in the background without your knowledge. Removing programs you don't use can help restore your computer's performance.
2. Install and run antispyware software
Most programs can be removed using the Add or Remove Programs function accessible from Control Panel, but spyware programs are more stubborn. Windows Defender (a free download from Microsoft) or another antispyware program can detect and remove these programs. You should always have an antispyware program installed, because spyware might install itself on your computer without your knowledge. After you install the antispyware program, run it to detect and remove any unwanted programs.
3. Free up wasted space
Removing unused programs is a great way to free up disk space, which will speed up your computer. Another way to find wasted disk space is to use the Disk Cleanup tool.
To run the Disk Cleanup tool
1. | Click Start, and then click My Computer. |
2. | Right-click Local Disk, and then click Properties.
|
3. | On the General tab, click the Disk Cleanup button. Disk Cleanup will spend a few minutes examining your disk.
|
4. | The Disk Cleanup dialog box will appear. Select each of the check boxes in the Files to delete list, and then click OK.
|
5. | When prompted, click Yes. Disk Cleanup will spend several minutes removing these files, which will provide you with more space.
|
If you have more than one hard disk drive, repeat this process for each hard disk drive listed in My Computer.
4. Defragment your hard disk drive
Sometimes, a newspaper article skips from the front page to somewhere in the middle of the paper. You have to stop reading the article and flip through the paper to find the page on which it continues. You could read the article much faster if it were printed on a single page.
Files on your computer can either be fragmented, like newspaper articles, or unfragmented, like a book. Over time, more and more files become fragmented. When a file is fragmented, it takes longer for the computer to read it because it has to skip to different sections of the hard disk drive—just like it takes you a few seconds to find a page in the middle of a newspaper.

Defragmentation improves your computer's performance by reorganizing your files.
While fragmentation looks complicated, it's easy to defragment your computer.
To defragment your computer
1. | Click Start, and then click My Computer.
|
2. | Right-click Local Disk, and then click Properties.
|
3. | Click the Tools tab, and then click Defragment Now.
|
4. | The Disk Defragmenter appears. Click your hard disk drive, and then click Defragment.
|
5. | Disk Defragmenter will work for at least several minutes, although it might take several hours. When prompted, click Close.
|
If you have more than one hard disk drive, repeat this process for each hard disk drive listed, starting at step 4.
5. Disconnect unused network connections
If you have, or ever have had, a network with more than one computer, you probably found it useful to share files between the computers by mapping a network drive. Mapping network drives allows one computer to read and write files to another computer's hard disk drive as if they were directly connected to each other.
The problem with network drives is that Windows XP will attempt to connect to the network drive when it starts up. If the remote computer does not respond immediately, Windows XP will wait, which will slow down your startup time. Additionally, some programs will attempt to connect to the network drive when you browse for files and folders. If you have ever tried to open a file and had to wait several seconds, it is probably because the program was trying to establish a network connection—even if the file you are opening is on your local computer.
To reduce the problem, disconnect any unused drives
1. | Click Start, and then click My Computer.
|
2. | On the Tools menu, click Disconnect Network Drive.
|
3. | Select the network drives that you no longer need, and then click OK.
|
Performing the five steps in this article once a month will help you keep your computer running at peak performance.
How Do Computers Work? - A Simple Explanation
 How Do Computers Work? - A Simple Explanation
How Do Computers Work? - A Simple ExplanationSo how do computers work? For a computer to accomplish any task, it needs three things: Hardware, software, and an input.
Computer Basics
Hardware is the machine itself. Your desktop or your laptop, and any other physical device connected to your computer either to make it work or help it function better. You need the hardware so you have something work on, You cannot perform a task on thin air, you will need something to put and store information into. These are the stuff you usually see on computer parts catalogs on the Internet when you are searching for computer parts online.
Hardware includes your CPU, monitor, keyboard, and mouse. There are countless peripherals that can be added to your PC. There are USB devices like fans, light, and others. Others attachment even enables the user to watch TV on the computer. There are just so many gadgets that you can connect to the computer nowadays.
Software is the program you install on the hardware to make it work. Your laptop is useless if you don’t have any software in it. It is just a piece of plastic and metal with a screen, nothing else. Softwares are developed to make our lives easier. They are designed to help us with a certain problem or area in our life. There are softwares for word processing, video and photo editing and just about anything.
The most basic software you will need to use your computer is the operating system, OS as it is commonly referred to. These programs is needed to boot your pc in its useable stage. After you install your OS, you can then add certain softwares for specific tasks.
And finally, the input. It is the information you enter on the computer. It is commonly the human part of the three factors. It’s the letters we type on the word processor, or the CD we put on the CD-ROM. These are all data or information that is processed by the hardware and software to produce outputs that we want.
So the trinity is complete. That’s basically it. Although there are so many enhancements and programs that are available for use, these three are the only thing needed to make a computer work. Well, of course you need power to turn the computer on.
Java Server PAges (JSP)
Servlet are powerfull and sometimes they are a bit cumbersome when it comes application logic and a lot more cade that handles output formatting. This can make it difficult to separate and reuse portions of the code when a different output format is needed.
There are many JSP tags such as :
1. JSP directive denoted by <%@,
2. Scriplets indicated by <% ... %> tags and
How PCs Work
When you mention the word "technology," most people think about computers. Virtually every facet of our lives has some computerized component. The appliances in our homes have microprocessors built into them, as do our televisions. Even our cars have computers. But the computer that everyone thinks of first is typically the personalcomputer , or PC.
A PC is a general-purpose tool built around a microprocessor. It has lots of different parts -- including memory, a hard disk, a modem, and more -- that work together. "General purpose" means that you can do many different things with a PC. You can use it to type documents, send e-mail, browse the Internet and play games.
PCs trace their history back to the 1970s, when a man named Ed Roberts began to sell computer kits based on a microprocessor chip designed by Intel. Roberts called his computer the Altair 8800 and sold the unassembled kits for $395. Popular Electronics ran a story about the kid in its January 1975 issue, and to the surprise of just about everyone, the kits became an instant hit and the era of the personal computer began [source: The Computer History Project].
A few years later, the dynamic duo of Steve Jobs and Steve Wozniak unleashed the Apple II computer on the world. From that point on, the personal computer really began to take off. Other manufacturers followed suit, and soon there were computers from Commodore, Atari and Texas Instruments. Not long after the debut of the Apple II, IBM got into the personal computer game












